INTRODUCTION
The Kill Chain model is a widely used framework for understanding the stages of a cyberattack, from initial reconnaissance to post-exploitation activities. The Kill Chain model essentially breaks down the various steps of an attack conducted by a malign actor. In recent years, this model has also been applied to the realm of disinformation, which is the deliberate spread of false or misleading information with the intention of influencing public opinion or gaining some other advantage.
Understanding the various stages of the disinformation "Kill Chain" can help individuals and organizations better protect themselves against these types of campaigns.
FIVE CRUCIAL STAGES
The Kill Chain model of disinformation is composed of five key stages, which will be described and analyzed in the section that follows.
The first stage of the disinformation kill chain model is reconnaissance, where the attacker identifies their target audience and gathers information about them.
This can include identifying vulnerabilities and weaknesses in their belief systems or gathering personal data about them to tailor the messaging of the disinformation campaign. The attacker may also seek to identify potential allies or influencers who can help amplify the message.
The second stage is weaponization, where the attacker creates or modifies the content that will be used in the campaign. This may involve creating false or misleading stories, images, or videos, or repurposing existing content to fit the desired narrative.
The content may be designed to play on the emotions of the target audience or to exploit pre-existing biases or divisions.
The third stage is delivery, where the attacker chooses the channels through which to disseminate the disinformation. This can include social media platforms, websites, or messaging apps, among other channels. The attacker may also use tactics such as fake accounts or bots to amplify the message and make it appear more widespread than it actually is.
The fourth stage is exploitation, where the disinformation is used to achieve the attacker's goals. This can range from influencing an election to causing social unrest to discrediting a particular individual or group. The success of the campaign may depend on the level of engagement it generates from the target audience, as well as the level of coverage it receives from traditional media outlets.
The final stage is post-exploitation, where the attacker may attempt to cover their tracks or maintain a level of control over the situation. This can include denying involvement in the campaign or using further disinformation to divert attention away from the original campaign.
EXPANDING THE TOOLBOX OF COUNTERMEASURES
Malicious actors use tactics and techniques to manipulate the information environment, and understanding their behavior as a process, in the form of a Kill Chain model, can help expand the toolbox of countermeasures necessary to detect and prevent disinformation. To combat the kind of disinformation generated through the Kill Chain model it is indeed necessary to go beyond classic fact-checking and debunking of false information, which are suitable responses only when disinformation campaigns have already reached a wider audience. Instead, it is useful to understand the steps and techniques used by malicious actors to manipulate the information and detecting and preventing each stage of the Kill Chain model to neutralize the attack.
This approach can enhance capabilities for detection, analysis and attribution of Foreign Information Manipulation and 3Interference (FIMI) attacks. Early detection and response can in fact prevent FIMI campaigns from having an impact, and different responses are suitable for different stages of the Kill Chain model.
SEPARATING THREAT ANALYSIS FROM DISRUPTIVE RESPONSES
In order to achieve the systematic disruption of FIMI, it is important to consider two additional aspects. First, it is necessary to analyze the behavior and tactics used by threat actors to manipulate the information environment. Second, it is key to systematically develop and measure disruptive responses and understanding their potential negative effects. The proposed approach is to operationally separate threat analysis and disruptive response challenges while increasing information sharing to effectively counter FIMI attacks. Equally important to consider, the appropriate response to FIMI needs to be proportionate to the seriousness of the threat and the most efficient response to these disinformation campaigns can vary based on different contexts and political actors.
FIMI THREAT ANALYSIS: AN ANALYTICAL FRAMEWORK
How is it possible to analyze FIMI threats? A useful point of departure is the ABCDE analytical framework proposed by James Pamment. The ABCDE framework differentiates FIMI incidents in terms of actors, behaviors, content, degree, and effect. This model therefore constitutes a helpful mnemonic for a comprehensive analysis and understanding of FIMI incidents and can be a useful tool to reveal cross-incident patterns by malicious actors.

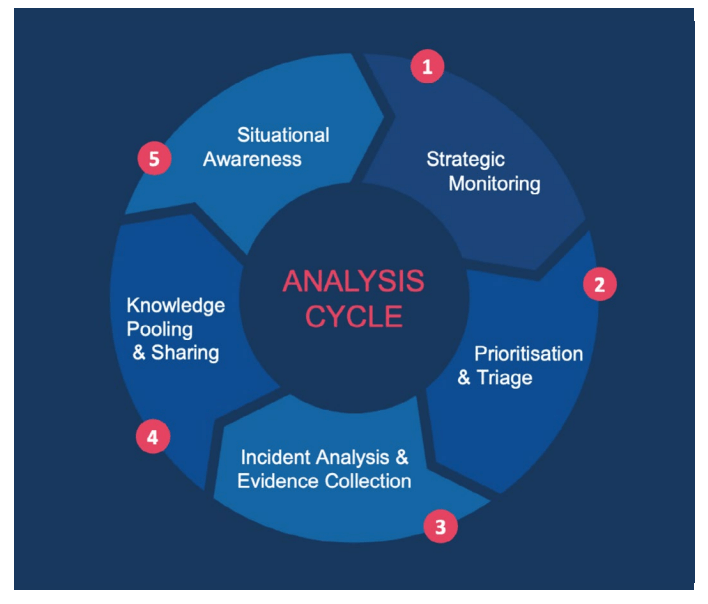
To further deepen the analysis of FIMI threats, it is possible to employ the Analysis Cycle. The Analysis Cycle is a methodology that helps systematically analyze and disrupt malign interference and disinformation while providing insights for quick reactions. The cycle consists of five phases: (1) Strategic Monitoring, which involves mapping the ecosystem of known FIMI assets used by a threat actor; (2) Prioritization & Triage, which filters the activity of FIMI channels to high priority and potentially harmful instances; (3) Incident Analysis & Evidence Collection, which focuses on open-source analysis and encoding data according to taxonomies; (4) Knowledge Pooling & Sharing, which maximizes the short- and long-term utility of the analysis; and (5) Situational Awareness, which continuously optimizes and reflects on the previous steps. By following this analytical approach, it is possible to gain an in-depth understanding of how threat actors attempt to manipulate the information environment, identify weaknesses in their behavior, and address societal vulnerabilities.
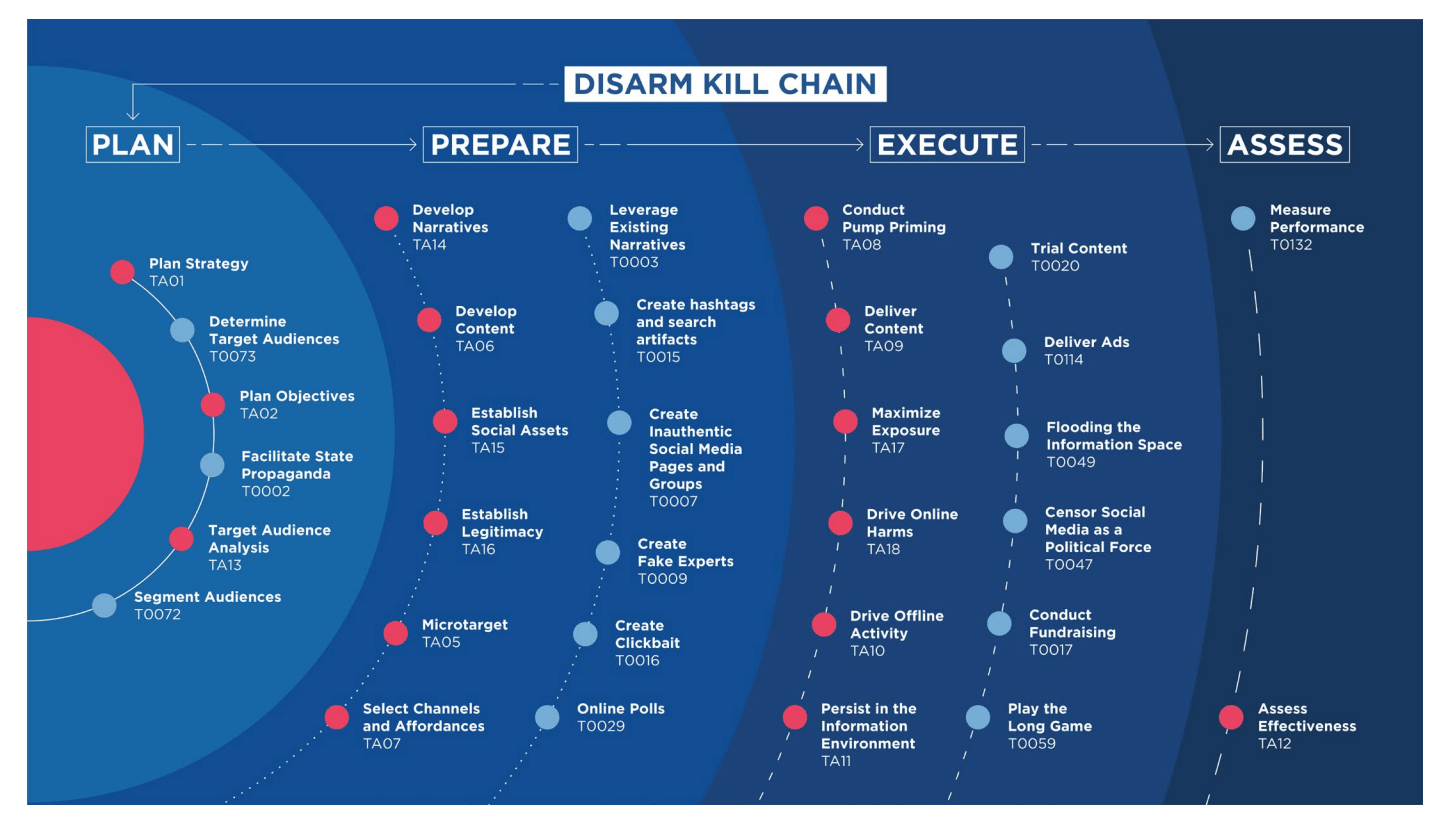
Furthermore, a taxonomy of the tactics, techniques, and procedures (TTPs) used by threat actors to conduct disinformation campaigns is highly needed. The taxonomy should be agile, conceptually structured, and open source to allow for maximum stakeholder inclusion and adoption. The DISARM foundation's Kill Chain taxonomy is currently the only framework that fulfils these criteria and provides a foundation for a community-led conversation on best practices. The taxonomy is structured hierarchically by phases, tactics, and techniques, and each phase includes multiple tactics, which in turn contain multiple techniques. The framework represents the state-of-the-art of understanding FIMI operations, but it will continuously need to be updated and optimized. The analysis of TTPs allows us to understand how threat actors conduct their operations and helps attribute attacks by establishing a threat actor's modus operandi or "behavioral fingerprint". Detecting and disrupting TTPs early in the kill chain is one of the main ways to counter an attack.
CONCLUSION
In conclusion, understanding the stages of the disinformation kill chain can help individuals and organizations better protect themselves against these types of attacks. By identifying vulnerabilities and weaknesses in belief systems and personal data, it becomes possible to develop appropriate countermeasures that will better prevent an individual from being manipulated into taking action based on false information. In addition, identifying the channels through which disinformation is likely to be disseminated and the tactics used to amplify it can help individuals and organizations better protect themselves from these types of campaigns.